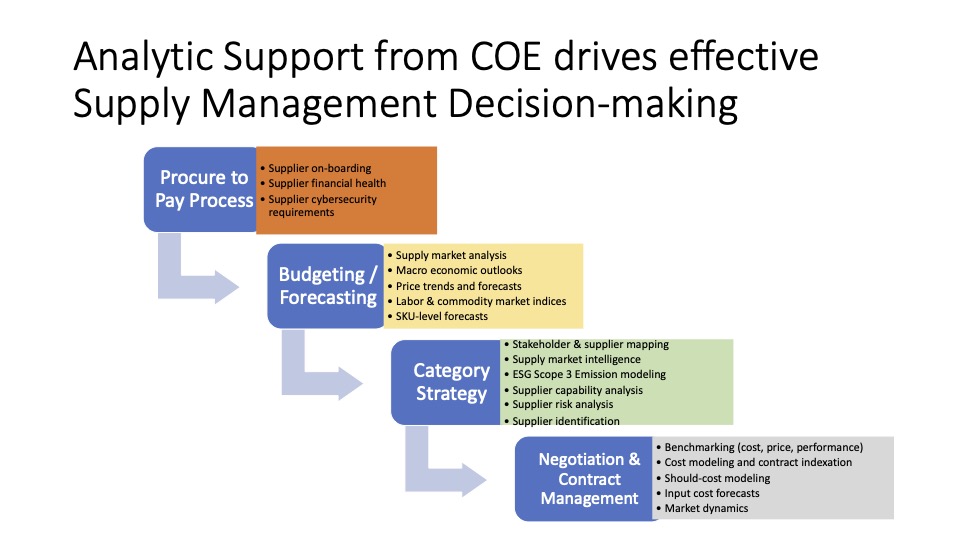
Your Suppliers are Vulnerable to Cyberattacks, and so are You…
An increasing vulnerability in today’s supply chains is the threat of cybersecurity intrusions. While many large organizations have sought to bolster their internal systems through multiple layers of cybersecurity preventive measures, they often overlook a major source of vulnerabilities: their network of small and medium sized suppliers, that are connected to their systems through supplier portals, EDI, electronic hubs, and even plain emails.
A recent review of the supply chain resilience literature advocates that the concept of resilience should be extended to the broader concepts of persistence, adaptation, and transformation (Wieland et al., 2023). Persistence is the act of improving the status quo, whereas adaptation involves improved integration with the ecosystem, such as managing slow feedback loops to react more quickly to disruptions. Transformation is more about enabling collective action and learning within the network. This latter framework is important when thinking about improving preparation for supply chain cybersecurity measures, as the literature largely focused on persistence within the firm. This is relevant, because of what is described as negative supply chain externalities. That is, the actions taken by a supplier operating at one tier creates potential problems for a firm operating at another tier (often the focal firm). Resolving this might rely on the supplier making investments that do not primarily benefit them but benefits the focal firm .
Most cybersecurity research falls into the “persistence” category, which generally refers to the management of the status quo. For instance, security executives often rely on cybersecurity standards to guide their organizations in managing cybersecurity risk, while providing a set of best practices to follow. These standards also support communication among stakeholders by using a common vocabulary.
Supply chains today encounter cybersecurity threats around intellectual property, sensitive data and cloud technology. These threats frequently originate from a third-party supplier with inadequate cyber protections in place. Most firms depend on third party suppliers for daily operation, yet many of these do not adopt the same cybersecurity protections and processes as the buying firm. Third party suppliers have privileged access to a firm’s internal data and systems, introducing a significant risk. Research on best practices in data sharing suggests that common best practices advocate high levels of supplier data sharing, through a variety of electronic hubs, portals, and integrated planning systems. However, many of these systems overlook actual cybersecurity technical details or practices associated with managing cyber threats. Our reviews suggest that supplier data protection capabilities remain nascent across many industries. However, due to a patchwork of laws and a propensity to minimize negative publicity, losses of operational data are not always reported, and in fact, many organizations may not be aware of data losses over time. In many cases, smaller suppliers do not have the resources to support dedicated personnel and formalized processes, and struggle to justify the investments necessary to support cybersecurity.
The fact that suppliers are increasingly becoming a face of vulnerability was noted by Richard George, former United States National Security Agency technical director of information assurance noted that ‘cybersecurity really is a supply chain problem’ . This statement was echoed by a recently published bipartisan Cyberspace Solarium Report (King and Gallagher, 2020) which focused most of its recommendations on supply chain issues.

Most of the research on cybersecurity approaches largely assume that data breaches involve external parties directly attacking the organization, but overlooks a critical element, namely that suppliers are often electronically integrated with companies, and represent a critical vulnerability that is often exploited by cybercriminals.
This gap in understanding goes beyond software protection. Cybersecurity in the supply chain requires many elements, including the policies, processes and technologies needed to protect networks, devices, systems, and data from unauthorized access or criminal use, while maintaining confidentiality, integrity, and availability. Because these elements are so broad in scope, managers have expressed the fact that cybersecurity concerns are often in conflict with organization initiatives to increase supply chain information integration . Accessibility to data versus security concerns are an important emerging issue, as many industries seek to integrate their suppliers electronically through digital transformation. Both the public and private sector must weigh whether security interferes with the use and utility of the product or costs more than the market will bear . With the proliferation of data sharing, and increased email in work-at-home environments, accessibility of information has become a major priority . Many organizations are encountering massive security breaches resulting from spyware, phishing attacks, ransomware, and other malware. Most companies work with thousands of suppliers, which introduces a significant set of vulnerabilities. As the growing number of external suppliers and service providers in the supply chain broadens, the attack surface for cyber intrusions also increases.
To mitigate these risks, businesses are encouraged to implement robust cybersecurity clauses in supplier contracts. These clauses establish clear expectations and responsibilities regarding cybersecurity practices, ensuring that both parties are committed to maintaining strong defenses . Additionally, organizations should regularly audit their suppliers’ security measures and limit access to sensitive data if possible.